
Windows’ built-in “Run-As” command allows you to launch a program as a different user account than the one currently active, However, runas.exe cannot be fully automated as it requires that the user typein the password for the alternate account. RunAsTool is portable freeware which allows standard users to run a specific program with administrator privileges without the need to enter the administrator password. This allows you to provide standard (non-admin) users with access to programs that require admin rights.
Under a restricted account, some programs may not run correctly due to missing administrator rights, therefore many users are given administrator accounts, making the system more vulnerable to malware, viruses and other security risks. With RunAsTool, you can correct this.
To run Properly RunAsTool need to install on a windows system which has an Administrator account with password.The login information for the application like username and password are read from an encrypted file – You don’t have to worry about your Admin Password.
RunAsTool v1.5 – What’s New – (Freitag, 2. September 2022)
1. [Added] – ability to attach a file in network location (\\BlueLife\ExampleFolder)
2. [Added] – option to reset previous list (/R) for import Cmd parameter
3. [Added] – parameter to uninstall program (RunAsTool.exe /Uninstall)
4. [Fixed] – The text in the program interface is tiny
5. [Fixed] – Improvements in the code of the program
6. [Fixed] – A small Bug in parameter and a character corruption in import parameter information
How to use
With RunAsTool there is no need to use a CMD prompt or any parameter in order to allow a standard user to run a program with admin rights. Just download, extract, and launch RunAsTool.
1) Administrators In standard user account:
Launch RunAsTool and choose an admin account (if there are more than one) and type in the associated admin password.
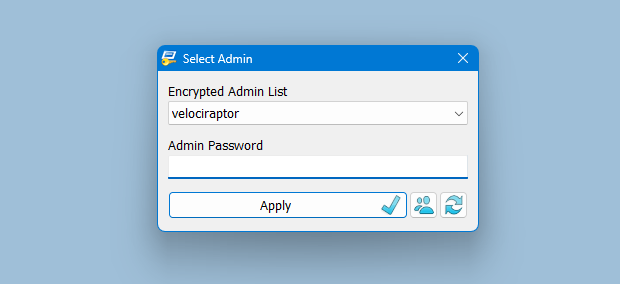
RunAsTool has two user interfaces (UI). One for administrator accounts and one for standard users. (Standard users aren’t able to use the admin UI). In the admin UI, you can easily drag and drop any program(s) into the UI in order to give it admin privileges. Standard users can also create application shortcuts.

To change the places of the icons in the interface, simply drag them on each other. RunAsTool has several useful options. For example, “Run with default rights”, “Run as limited user”, as well as the ability to show, hide, minimize, or maximize the launched window(s). As a security check, administrators can use “check the file size before run” feature. If a restricted user attempts to rename another program in order to run it with admin rights (a.k.a. “spoofing”), this option will prevent the user from doing so.
2) Administrators In Administrator user account:
Admins can easily add program(s), then right click it/them and create a shortcut on the standard user’s desktop.

Administrators can also easily import and export program lists. Just click File–>Menu and choose Import or Export. This is useful to create a list once and use it again later.

Standard users have two options to use an allowed program(s) with admin privileges.
1) In the RunAsTool restricted UI, double-click any program to run it with admin rights.

2) If the administrator has allowed it, a standard user may click any program and create their own shortcuts, so that there is no need to launch RunAsTool every time. They can also use any shortcut which the admin has already created for them.
How to import a backup file to multiple computers

To backup your settings please use “File – Export List” Feature , you will get a .rnt file like this “20180426_173736_RunAsTool.rnt” the first numbers Indicates the current date , to import the backup file silently run the Cmd with Administrator privileges and use the following command
RunAsTool.exe "/U=Admin" "/P=PassWord" "/I=Import.rnt"
RunAsTool.exe /R "/U=Admin" "/P=PassWord" "/I=Import.rnt"
/R : Reset previous list
Admin : Account Name
PassWord : Account Password
Import.rnt : Backup file name
To simplify the whole process you can use a cmd or Bat file and use an Account credentials temporarily in it.
Supported operating systems: Windows 11 , Windows 10 , Windows 8.1 ,Windows 8 , Windows 7 , Windows Vista , Windows Xp
Supported languages: English , Turkish , German , French , Spanish, Vietnamese, Greek , Indonesian , Russian , Japanase , Persian , Arabic , Polish , Chinese (Simplified and Traditional) , Hungarian , Korean , Slovenian , Hebrew , Italian , Brazilian Portuguese ,Dutch (Nederlands) , Romanian , Catalan , Lithuanian
File: RunAsTool_x64.exe │ Virustotal
MD5: 38fcaa6fb65ce15c777132caf6e1056b
SHA1: c62ca48c1995cc657acac7c33705d9e0dc1c3997
File: RunAsTool.exe │ Virustotal
MD5: 899198029f9adc45094652dc9a629a99
SHA1: 60d5169c227500a56dd5555abaf951d996d4203c






hello, when I start the application, it tells me there is no administrator crypted account found.Create an administrator account and try again.etc…
How is it ? I am the only user and I always thought I was admin, even if recently something changed as some folders or actions ask me permissions or deny me authorizations to enter folders etc…
Now your app tell me to see users account and mine is under Administrator so what can I do ? should I change it to ‘others=> administrators group’ ?
thank you by advance
@Virgulto : Do you use a very long Password ?
@Aladar : No, Admin right is mandatory
today, my win 10 pro has completed an update. After login, i always run a batch file. For the first time this app (1.0.0.0) ask me admin password but don’t accept my administrator password. I switched to Administrator, enter the correct password but RunAS don’t accept the password. I also tried 1.4.0.0. How can I fix/reset it? Thank you
Hi, the configurations that I setup by a user with admin privileges, will be still effective even if such user losts his admin rights?
Could you please try it
Hi!Can elevated shortcut which is made by runastool autostart in normal user account(non administrator account)?
Hi,
I try to import settings through a script launched by GPO (startup machine, so with admin rights).
The script is working well when launched by user with admin rights (but not Administrator). It seems that the problem comes from UAC.
Am I missing something ?
Thanks a lot for this tool.
@Quantdox, just to explain.
The UAC was implemented for all those specialist, who use an administrator account for his daly work, but this is not recommended since computer exist.
In most big environment the UAC is turned off, because an expert administrators know what he do and work only under his account to change some specific system settings.
The job of the UAC is only to protect administrators who know NOT what they do
I like this runas tools. You also find a list of all with comparison on Web Link …
Network drives don’t show up in elevated programs?
This application is heavily bugged & it provides a great way to design exploits for any script kiddie or a nursery grade intruder. I suggest the software engineer to immediately stop hosting it.
Any sort of digital access should be under supervision. All OSes know this & which is why they have designed UAC because an admin is required to provide unrestricted access to a limited user under his supervision & no app can mitigate the unrestricted access problem. That’s just almost impossible.
Simple Exploit 1:- First any application launched will display a UAC notification & when clicked on “change on how these notifications appear”, one can change UAC settings which can’t harm standard users much but will push back Win-10, 8, 7 admins to old XP days.
Simple Exploit 2:- If someone downgrades to older .NET Framework below v3.0 then it causes faulty code to execute messing up file system permissions. Many times a standard user can easily change system folders permissions by taking advantage of this. Although the intruder wouldn’t know that when this faulty code executes itself.
Exploit 3:- Sometimes when a standard user clicks on “Launch edit mode” & clicks on “Manage user accounts” from 3/10 times the standard user can remove admin account. This faulty code also executes randomly. Sometimes it happens other times it doesn’t.
Simple Exploit 4:- 90% of programs easily provide application escape within their application. For example if a program requires admin privileges to be installed to a directory, the standard user when choosing a directory can easily right-click or shift+right-click anywhere & click on “Open command window here” & can open cmd.exe with admin privileges.
This isn’t the fault of this software, it’s the way Windows kernel is designed which is why it becomes an easy & great platform for security intruders or what these people call as hackers.
Iv locked myself out my admin will this be of any use ? Thanks
Actually We have developed it for Home users but there are lots of local Domain Admins request , will think about this
It’s a petty we can’t add local Domain Admins to this application…
Hello,
Our local admin password has 39 characters, a lot of spaces et some ‘ and !. Impossible to pass the first “Select Admin” screen with that kind of password.
Is there limitations?
Thank you!
Really nice application!! Thanks a lot!!!
It’s a petty we can’t add local Domain Admins to this application…
Would be perfect there after.
Really nice app… BUMP to the developer…
Wonderful app, thanks a ton !!!